Integration with Okta#
If your company uses Okta for identity management, the integration with NVIDIA can be based either on OpenID Connect (preferred) or on SAML.
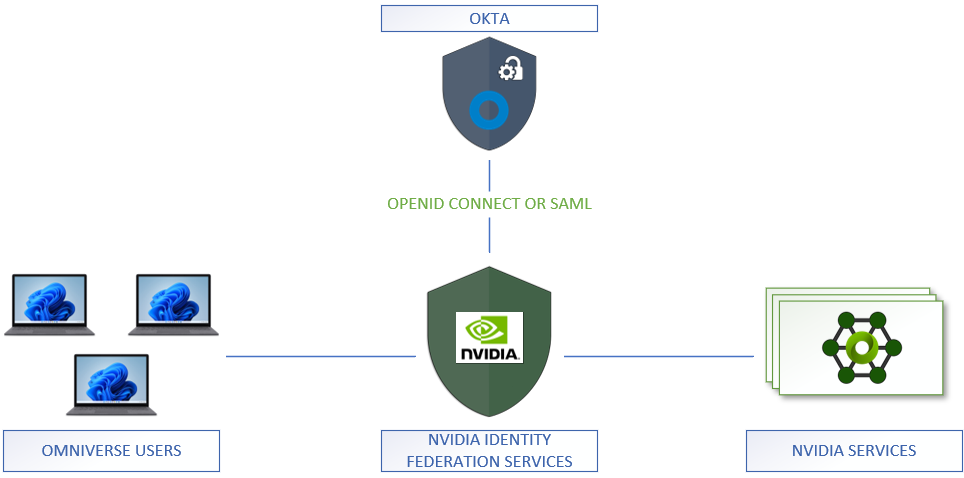
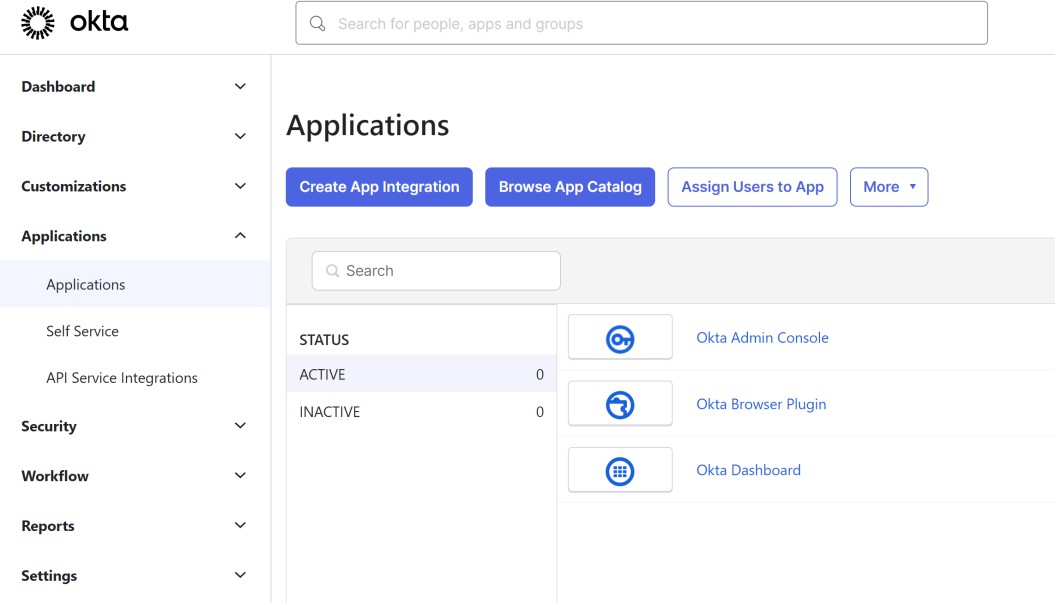
The following sections provide instructions for both options. The starting point is the Create App Integration button on the Applications page on the Okta admin console.
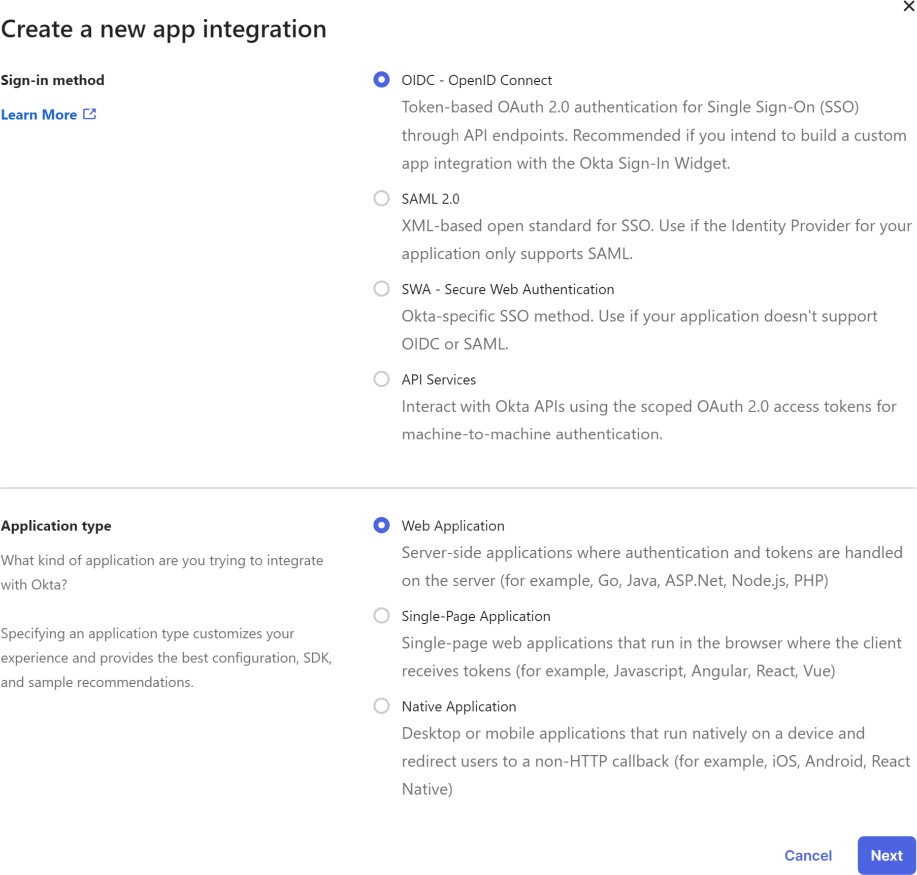
Integration via OpenID Connect#
Select the OpenID Connect sign-in method and the Web Application type.
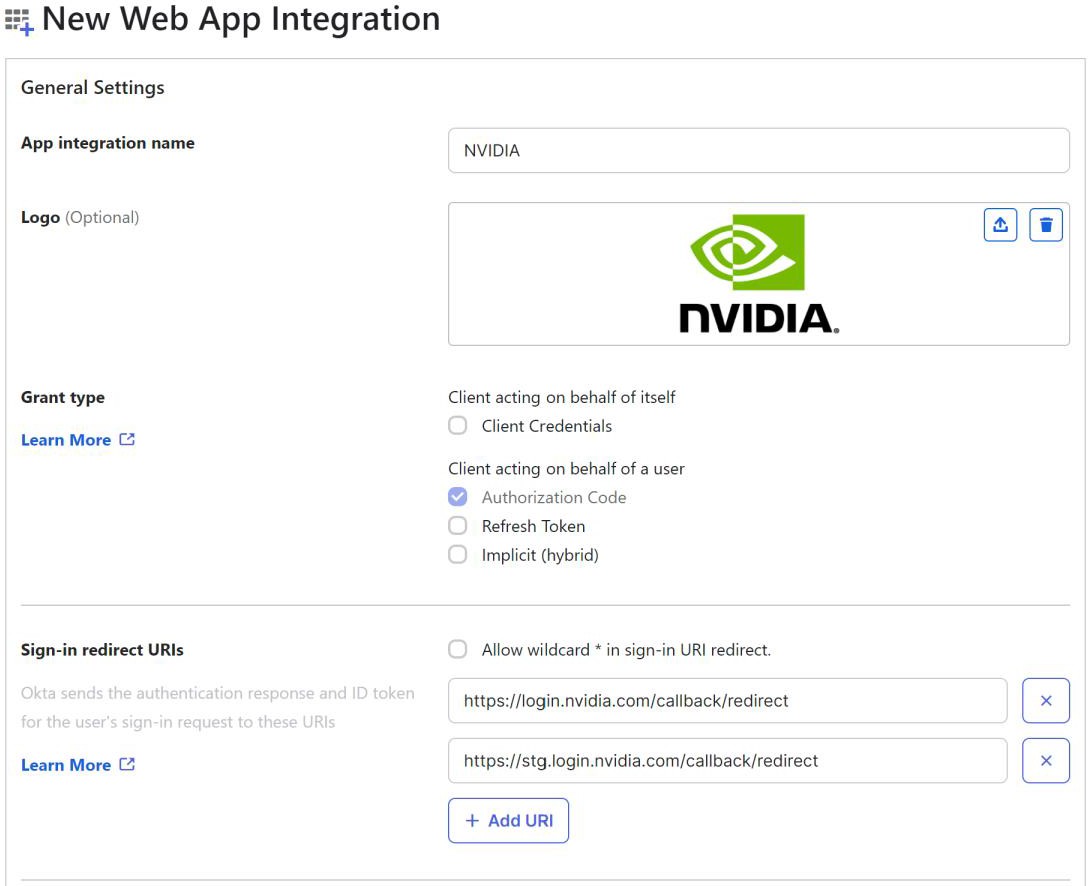
Assign a name to the application (e.g. NVIDIA) and specify the following two redirect URIs, the first for the integration tests and the second for production:
If you want to include an icon for NVIDIA, you can fetch it from here.

At the bottom of the page, chose which users should be able to log in to the NVIDIA services and then save.
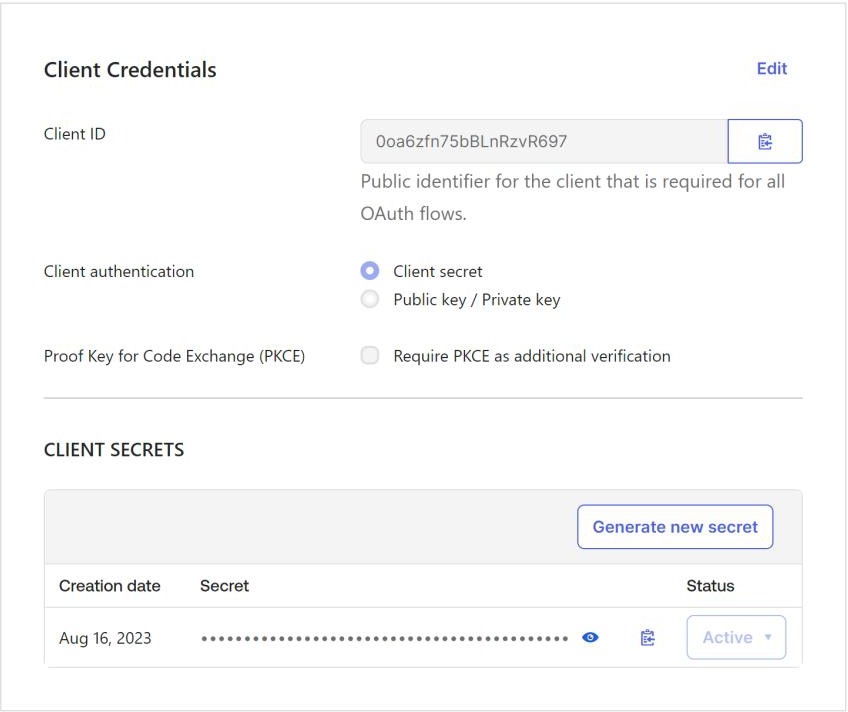
On the next page, copy the client id and client secret that have been auto-generated. You will need to hand over these values to NVIDIA.
Select the Sign On tab and then find the OpenID Connect ID Token panel.
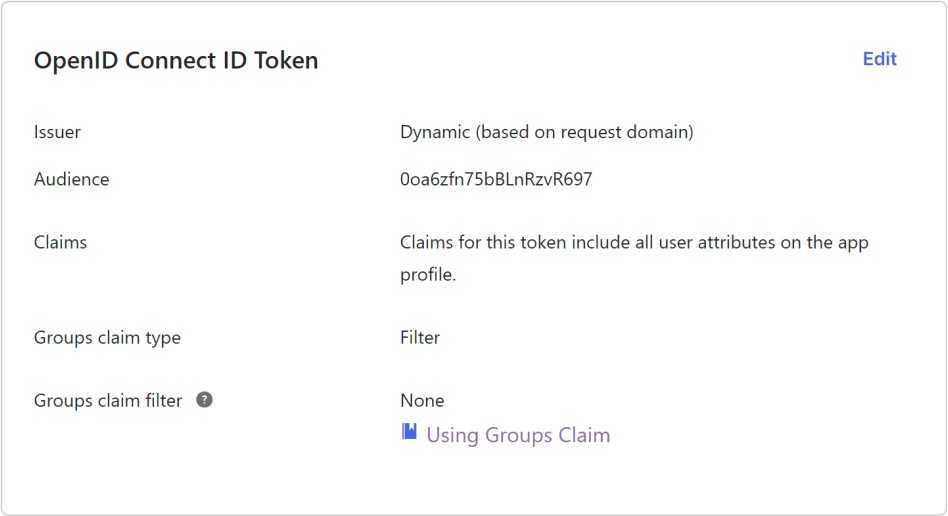
Click Edit to enter the edit mode and select what user authorization groups you want to share with NVIDIA. Please leave the name of the claim used to report groups to its default value (i.e. groups).
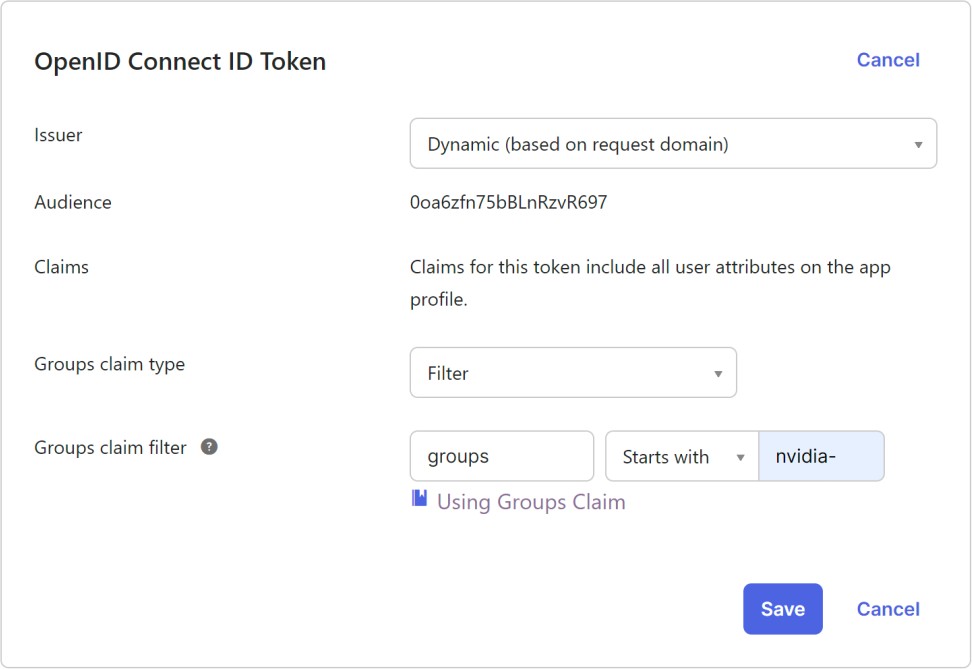
Sharing the group memberships with NVIDIA is useful because it allows you to indicate to certain NVIDIA services what authorizations/privileges/roles of each of your users.
You can add or remove groups at any time. With Okta, one practical way to ensure clarity and flexibility is to use one common prefix such as nvidia- for all the groups that you intend to share with NVIDIA.
Integration via SAML#
Select the SAML sign-in method:
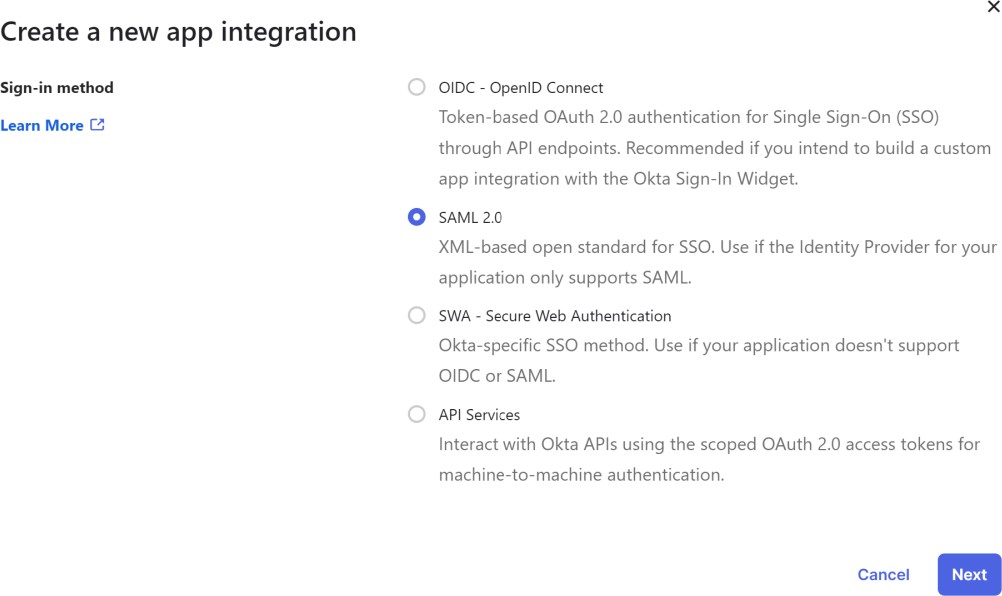
Assign a name to the application (e.g. NVIDIA). If you want to include an icon for NVIDIA, you can fetch it from here.

Enter the NVIDIA single sign-on URL and entity identifier. Leave all the rest to its default values.
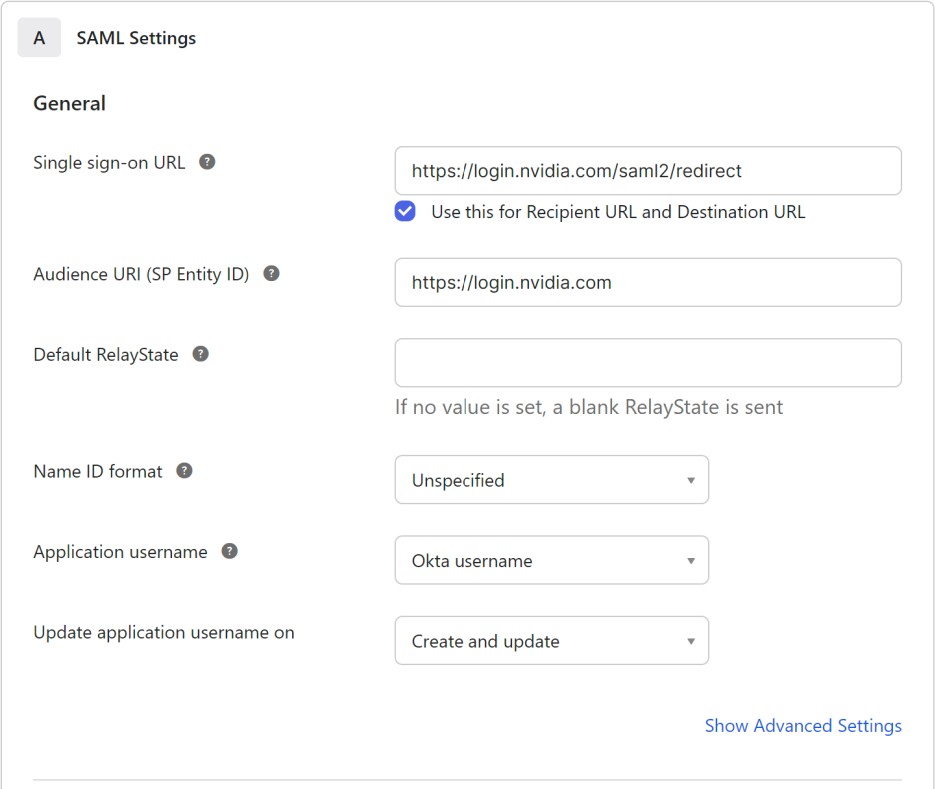
The NVIDIA identity federation system uses the following identifiers and URLs. Please use the values for the production environment unless you have been instructed otherwise.
NVIDIA environment |
Entity ID |
Assertion Consumer Service URL |
|---|---|---|
Production |
|
|
Pre-integration tests |
|
|
At the center of the page, find the Attribute Statements panel. Configure attribute name email to export the user email and attribute groups to export the user group memberships.
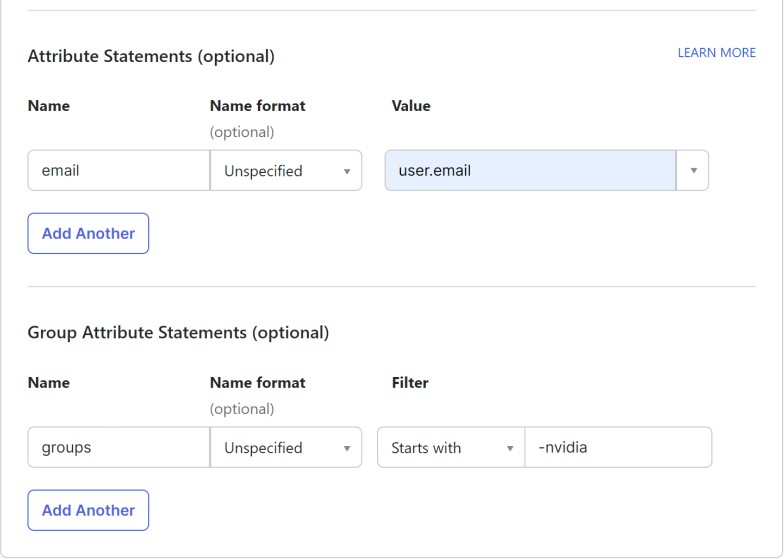
Sharing the group memberships with NVIDIA is useful because it allows you to indicate to certain NVIDIA services the authorizations/privileges/roles of each of your users.
You can add or remove groups at any time. With Okta, one practical way to ensure clarity and flexibility is to use one common prefix such as nvidia- for all the groups that you intend to share with NVIDIA.
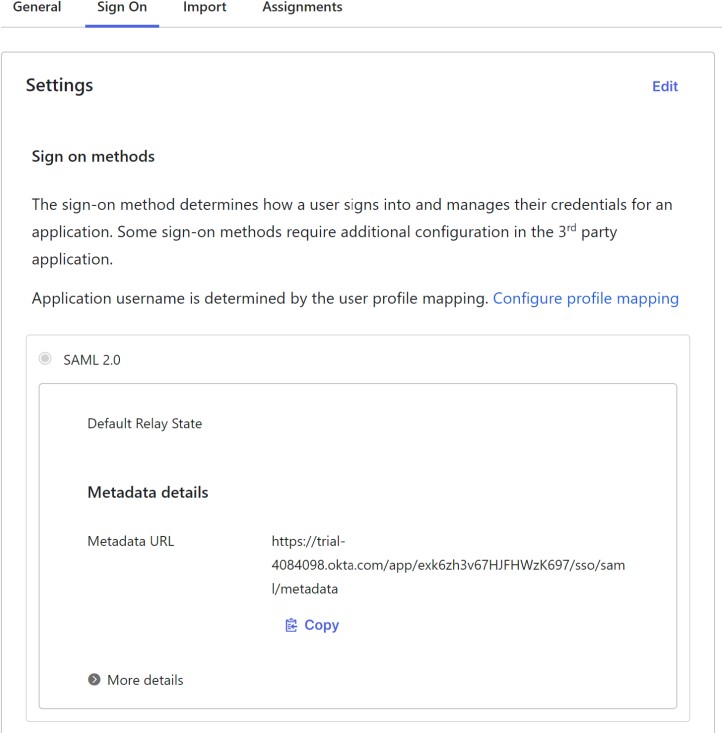
On the Sign On tab, find and copy the metadata URL that has been auto-generated. You will need to hand over this URL to NVIDIA.
Information to Be Provided to NVIDIA#
The following tables specify the information that NVIDIA needs to set up the integration. The first table is relevant if you have opted to use OpenID Connect. The second table is relevant if you have opted to use SAML.
Integration via OpenID Connect
Info |
Comments |
|---|---|
Your OpenID Connect provider configuration URL |
Typically this has the form |
Client id and secret assigned to NVIDIA |
See :ref:this<okta-integration> section |
Integration via SAML
Info |
Comments |
|---|---|
Metadata URL of the application assigned to NVIDIA |
Typically this has the form https://<your-okta- domain>.okta.com/app/<app-id>/sso/saml/metadata See section 7.2 |
Attribute names used for the primary email and group memberships |
See section 7.2. This is necessary only if the chosen attribute names are different from email and groups |