Nucleus Tools#
Latest release: Nucleus Tools 1.2.3
Overview#
Nucleus Tools is a collection of utilities delivered via a Docker container providing advanced capabilities and functionality.
Nucleus Tools includes the following:
Tool/Command |
Description |
|---|---|
|
A tool to dump backups of Nucleus instances. |
|
A tool to download subtrees of Nucleus instances. |
|
A utility to manage backups and subtrees downloaded via the |
|
A tool to upload backups and files to Nucleus instances. |
|
Tools to delete and list files and directories of Nucleus instances. |
|
A utility to sanitize user information from Nucleus instances for data privacy regulations (e.g., GDPR). |
Note
Nucleus Tools is obtained through the NVIDIA Licensing Portal and available to Enterprise customers only.
For additional Nucleus Tools documentation, use the following command to mount the container and display the in-container help on a Docker enabled server: (This can be run on your Enterprise Nucleus Server.)
export NUC_TOOLS=[PATH_TO_CONTAINER] sudo docker run --rm -p 8888:80 -e "ACCEPT_EULA=Y" $NUC_TOOLS docs
Once the container is running, visit the IP Address or Hostname of the server in a web browser on TCP 8888.
Using Nucleus Tools#
To use one of the Nucleus Tools, use the following command to mount the container and execute the tool on a Docker enabled server: (This can be run on your Enterprise Nucleus Server.)
export NUC_TOOLS=[PATH_TO_CONTAINER] sudo docker run --rm -e "ACCEPT_EULA=Y" $NUC_TOOLS (command)
For example, to run the ls tool, use the following command:
export NUC_TOOLS=[PATH_TO_CONTAINER] sudo docker run --rm -e "ACCEPT_EULA=Y" $NUC_TOOLS ls
All included tools offer additional help and documentation by appending -h after the tool’s name.
Nucleus User Sanitization#
For the requirement of sanitizing a user’s personally identifiable information (PII) / user account from a Nucleus instance, the Nucleus Tool scrub_users is available.
Warning
User sanitization requires an Enterprise Nucleus Server running 2023.2.2 or greater. (Prior versions of the Enterprise Nucleus Server software are not compatible.)
The usage syntax for scrub_users is:
export NUC_TOOLS=[PATH_TO_CONTAINER] sudo docker run --rm -e "ACCEPT_EULA=Y" $NUC_TOOLS scrub_users -u omniverse -p $omniverse_admin_password $server_hostname_or_ip $user_to_sanitize --do-it
For example, if your omniverse password is password1, your Enterprise Nucleus Server hostname is nucleus.example.com, and the user to sanitize is jdoe, the command to use is:
export NUC_TOOLS=[PATH_TO_CONTAINER] sudo docker run --rm -e "ACCEPT_EULA=Y" $NUC_TOOLS scrub_users -u omniverse -p password1 nucleus.example.com jdoe --do-it
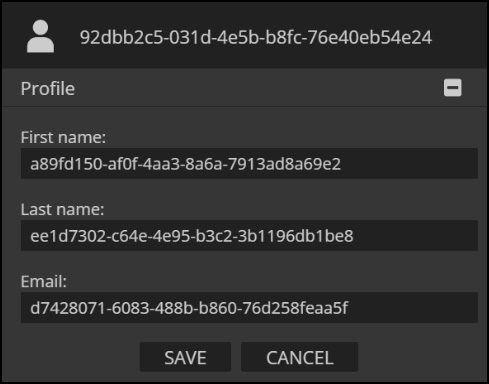
Once complete, logging into the Enterprise Nucleus Server will display the sanitized user. While the information generated is random, the sanitized user will resemble the following sample:
Warning
Nucleus user sanitization is not reversible. Once a user has been sanitized, it cannot be recovered unless the server is restored from a backup.
Note
Nucleus user sanitization can be run on local Nucleus accounts and accounts created through Single Sign-On integration. Nucleus user sanitization cannot be run on built-in or system accounts (e.g., omniverse).